

Keywords: Cyber-Informed Engineering, US Department of Energy, Idaho National Labs, Secure by Design, Industrial Cybersecurity, ARC Advisory Group.
The world of industry and critical infrastructure continues to struggle with allocating the right amount of resources to OT/ICS cybersecurity. In many cases, industrial cybersecurity is still seen as an add-on or something to be addressed after a system is designed, installed, and operational. The dearth of resources combined with an expanding threat surface in the form of increasing infrastructure attacks is increasing the adoption of secure by design principles.
Secure by design concepts have been applied to products, including security product certification schemes such as ISASecure for devices and host systems, and software development lifecycle practices of automation and operations management. The world of industrial software has applied secure by design concepts such as DevSecOps for many years. Efforts like ISA 62443-3-2, for example, are looking at cybersecurity system risk assessment and associated work processes, while 62443-4-1, focuses on product security development lifecycle requirements.
Industrial control systems and processes are highly complex beasts. You can either build a cage around them to try to keep them safe, or you can build increased resilience into them to make them more inherently secure. In reality, end users will need to do both. In terms of cost and effort, it’s much more effective to strive for inherent resilience in system design than to add layers of protection to address vulnerabilities. Traditionally, however, the domain of systems engineering and its role in cybersecurity was largely ignored. ICS cybersecurity was often not implemented until after the system has been designed and engineered. This is beginning to change.
The end user will add layers of protection to the existing system without giving much thought as to how to make the system more secure at the design and engineering phase. This is all changing, however, in large part because of an increased focus on cyber resilience by many national governments, including the US.
In 2023, the US national cyber resilience strategy was announced, which will “provide the resources and tools necessary to ensure effective cybersecurity practices are implemented across our most critical infrastructure.” As part of this overall effort, DOE through the Idaho National Laboratory (INL) and National Renewable Energy Laboratory (NREL), who have long been involved in the world of OT and industrial cybersecurity for the energy and manufacturing sector, has developed a methodology called Cyber-Informed Engineering (CIE), which uses design decisions and engineering controls to eliminate or mitigate avenues for cyber-enabled attack. CIE offers the opportunity to use engineering to eliminate specific harmful consequences throughout the design and operation lifecycle, rather than add cybersecurity controls after the fact. Focused on engineers and technicians, CIE’s goal is to create a culture of security that is closely aligned with safety culture.
According to INL, “CIE introduces cybersecurity considerations at the earliest stages of system design, long before the incorporation of software and security controls. It specifically calls on engineers to identify engineering controls and design choices that could eliminate attack vectors for cyber actors or minimize the damage they could inflict. This approach creates new opportunities for engineering teams—and not just cybersecurity teams—to secure the system using the physics and mechanics of engineering controls—not just digital monitoring and controls.”
CIE goes beyond just the engineering of systems to include support and incentivization for the adoption of CIE principles into “engineering curricula, certification programs, accreditation processes, and regulatory policies.” CIE is part of a broader strategy at INL, which it calls Consequence-driven Cyber-informed Engineering (CCE), a methodology specifically targeted at the nation’s critical infrastructure that incorporates a “think like the attacker” philosophy. CIE adopts a risk and consequence and risk-based approach to mitigating cyber threats.
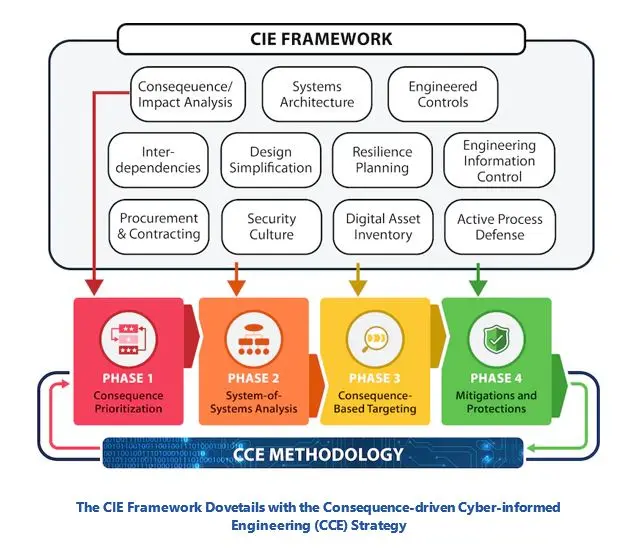
CIE is an approach that makes critical infrastructure more secure from cyber threats by incorporating engineering solutions into the system design from the start. Instead of adding cybersecurity measures after the design is finished, CIE allows the use of engineering to reduce or remove cyber-attack pathways—starting from the early stage of design and continuing throughout the system’s lifecycle.
CIE also provides additional ways to lessen the worst impacts of cyber-attacks and prioritizes these protections based on an analysis of the consequences of the cyber-attack. CIE is an engineering-based method that integrates cybersecurity factors into the creation, design, construction, and operation of any physical system that has digital connectivity, sensors, monitoring, or control.
ARC Advisory Group clients can view the complete report at the ARC Client Portal.
Please Contact Us if you would like to speak with the author.
You can learn more about cybersecurity at Industrial Cybersecurity Market Analysis Research

