

ARC Advisory Group research indicates that while many companies across a wide spectrum of industries have 
ARC discussed these challenges with Honeywell Process Solutions in a recent briefing about the company’s broad portfolio of industrial cybersecurity services. This provided an opportunity to delve more deeply into the new CyberVantage Managed Security Service capabilities the company presented at the recent 2018 Honeywell User Group meeting.
ARC developed the Industrial Cybersecurity Maturity Model to help industrial managers understand their cybersecurity challenges without having to become cybersecurity experts. This model shows the people, processes and technologies needed to ensure the security of industrial plants and infrastructure. It is also a useful tool for discussing the inadequacies ARC sees in many existing industrial cybersecurity strategies.
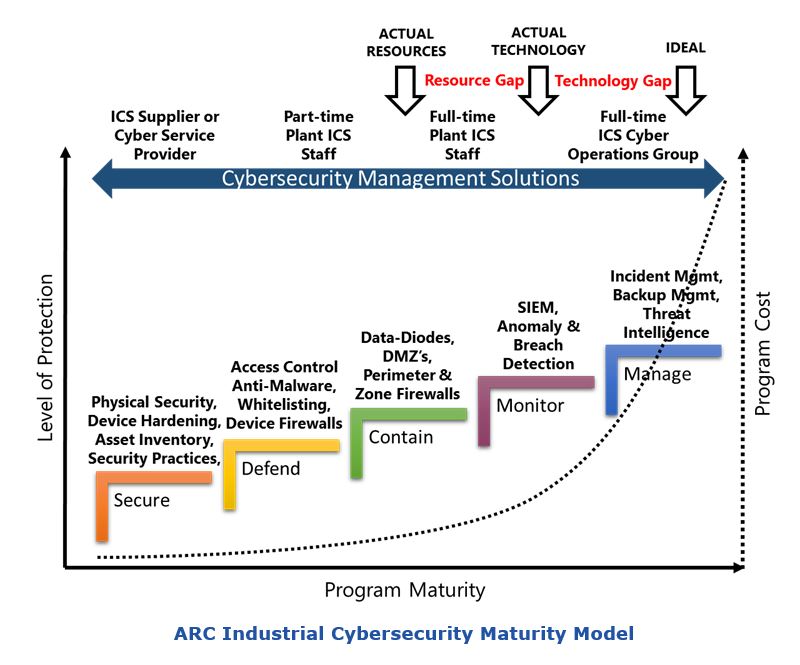
ARC’s research indicates that most companies are operating with significant security, technology, and resource gaps. Many facilities have invested in the passive, defensive technologies shown in the first three steps, but this is not adequate for operators of industrial plants and critical infrastructure. These facilities are at risk of sophisticated attacks by nation-states and cyber criminals and need the active defenses shown in steps four and five.
The gap in resources is even more troublesome as it affects companies in every industry. Most facilities lack the people and expertise to even maintain the technologies in steps one through three. This undermines the effectiveness of defenses in every step and leaves industrial managers with a false sense of security regarding their risk of a serious cyber incident.
Addressing the cybersecurity resource gap can be challenging for industrial managers. Plant staffs can be trained, but these people will still have other duties that keep them from attending to cybersecurity hygiene tasks. Efforts to augment staffs with qualified people are often frustrated by the global shortage of cybersecurity experts and high salary levels.
Large companies with internal security operations centers (SOCs) can address resource challenges through integration of corporate IT and OT cybersecurity programs; though integrating these often-disparate cultures has its own challenges. Large and small companies can gain similar coverage through use of third-party cybersecurity services. ARC endorses both approaches since either can help avoid potential gaps in control system expertise and local support.
Most companies will need a blend of all these approaches. Flexibility in the allocation of tasks among groups is another important issue to consider in discussions with corporate and external service providers.
Honeywell offers a broad portfolio set of industrial cybersecurity products that can help companies address their security resource gaps. This includes software solutions, professional services, and managed security services.
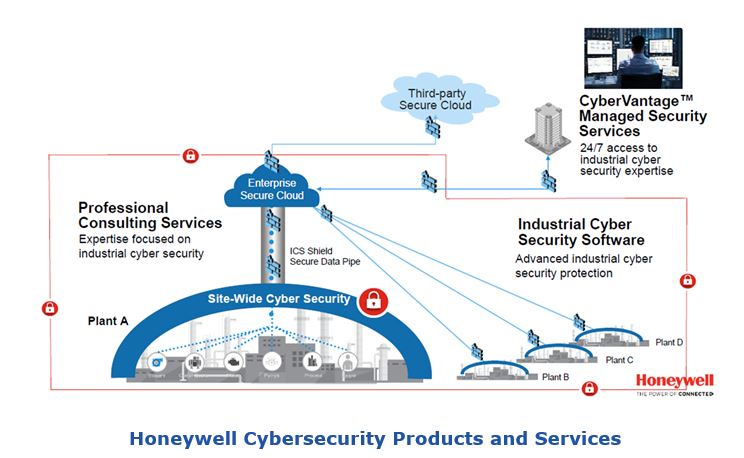
The company’s software products include Risk Manager, Secure Media Exchange and ICS Shield. The Risk Manager cybersecurity management solution provides continuous visibility of the security status of all system networks and devices (PCs and Honeywell process controllers). This can help managers understand their “real” security posture and reduce the workload for internal security resources. Secure Media Exchange can help companies defend systems against compromised USB devices used by operations and service personnel. ICS Shield provides secure, controlled remote access for internal and external resources as well as the ability to support patch management and remote monitoring. ICS Shield is being used by thousands of facilities around the world. Honeywell acquired the developer of ICS Shield, NextNine, in 2017 and uses this product as the foundation for secure delivery of its own managed security services.
Honeywell’s Professional Services is a large, global team of cybersecurity professionals who can provide on-site support for companies that want to establish or enhance the security of their control system environment. Services include site risk and vulnerability assessments and the follow up support needed to design, install, and configure appropriate defenses.
Honeywell CyberVantage Managed Security Services provide a way for industrial companies to address the many security tasks that are required to sustain security posture. This capability can also be used to enhance security defenses through active monitoring and response. Honeywell Managed Security Services are provided remotely on a 24/7 basis by collaborative teams of people located in three global SOCs.

According to the company, more than 400 customers already use CyberVantage Managed Security Services, including the company’s own Honeywell Chemical Divisions. Contracts are flexible and include any or all of the following support services:
Honeywell also reports that its SOCs provide support for a wide range of popular security products, including new anomaly and breach detection solutions, and non-Honeywell automation products. They also leverage advanced tools like SIEMs with Analytics and Playbooks to ensure efficient, seamless coverage across SOC teams. End users have complete control over the support they need and must approve all actions. This includes pre-defined notification lists and control of all actions through the ICS Shield monitoring and recording capabilities.
Securing industrial facilities is a critical issue. An incident can harm people, damage complex equipment, and jeopardize the very survival of an industrial organization. And these risks are rising as sophisticated attacks by cyber criminals and nation-states demonstrate the inadequacy of conventional defenses. Compromises of safety systems and other critical assets that have come to light in recent years show that these groups have the system expertise to inflict serious damage on industrial operations.
Lack of resources and expertise is undermining security in many industrial plants. Basic defenses are not being properly maintained. Suspicious events are not being promptly investigated. This situation is intolerable and unnecessary given the availability of professional cybersecurity support from companies like Honeywell. ARC cannot overemphasize how urgent it is to solve these problems.
If you would like to buy this report or obtain information about how to become a client, please Contact Us
Keywords: Industrial Cybersecurity, Honeywell Process Solutions, Managed Security Services, ARC Advisory Group.

