

Cybersecurity end users from major industrial companies shared their views on the challenges and benefits of converging IT and OT cybersecurity technologies.
Many industrial cybersecurity leaders are pushing for convergence of IT and OT Cybersecurity programs. They recognize that this can be a cost-effective way to address resource challenges, improve defenses against sophisticated cyber-attacks, and institute the end-to-end protection required for secure digital transformation. But many are unsure about how to achieve an effective convergence of people, processes, and technologies. What should be their final goal? How do they overcome cultural and technological differences?
The 2021 ARC Industry Forum included two workshops to help end users develop effective convergence strategies. Each workshop included polls of attendees on key aspects of IT/OT cybersecurity convergence and a roundtable discussion of the results and other issues. Roundtable participants included IT/OT cybersecurity leaders from various industries who shared what their own companies were doing.
This ARC insight discusses the workshop on technology convergence. A separate insight discusses the workshop on the convergence of cybersecurity people and processes.

Concerns about all these challenges were reflected in attendee responses to poll questions in the IT/OT cybersecurity technology convergence workshop. Panelists generally agreed that all of these were concerns, and they need to be addressed in a strategy that drives better overall cybersecurity. OT investments in technology that provides more connectivity with IT defenders and security operations centers (SOCs) was an essential step towards this goal.
Attendees and panelists also noted that top management sponsorship is critically important. While operational managers have been convinced of the need for cybersecurity, they still need to be translated into budgets for technology and resources. Top management support can raise the priority of cybersecurity in tradeoffs that managers must make in developing operational budgets.
Almost 70 percent of session attendees indicated that their companies were already on IT/OT cybersecurity convergence journeys, with a large percentage indicating that they were already converged. This is consistent with poll results in the IT/OT cybersecurity people and processes convergence workshop. Panelists in both sessions attributed this high level to different definitions of convergence.
ARC’s presentation at the start of both sessions addressed this issue through three different convergence models -- collaboration, integration, and unification. These models reflect tradeoffs between convergence and isolation goals. ARC also emphasized the need for strategies that incorporate all these models. The individual models provide a basis for establishing site-specific convergence goals and mile markers for journeys to fully unified programs.
ARC research consistently shows that most OT security people recognize the limitations of isolation-based strategies. 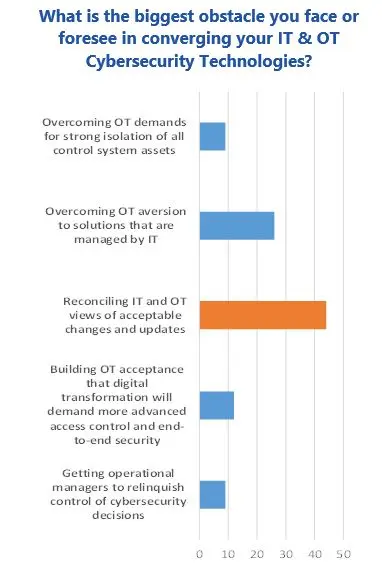 Sophisticated attackers can still find ways into OT systems and management of these compromises requires more advanced solutions and external support. Demands for connectivity are also growing, requiring investments in better management of privileged access and security of external systems and devices. The major concern is to ensure that OT has a proper role in decisions about how IT technologies are applied to ensure that basic OT constraints are respected.
Sophisticated attackers can still find ways into OT systems and management of these compromises requires more advanced solutions and external support. Demands for connectivity are also growing, requiring investments in better management of privileged access and security of external systems and devices. The major concern is to ensure that OT has a proper role in decisions about how IT technologies are applied to ensure that basic OT constraints are respected.
Poll responses and panelist comments support ARC’s research findings. Reconciling IT and OT concerns is much more important than concerns about isolation. Reluctance to adopt IT technology should not be an obstacle.
Poll results in this workshop suggest that the best opportunities for technology convergence center around solutions that address current OT security concerns. This includes tools that can reduce security management workloads, detect and manage sophisticated attacks, and extend network security capabilities. Surprisingly, remote access control was not considered a good opportunity.
While panelists generally agreed with these poll results, they noted several limitations. Remote access is one of the most important challenges for OT today, and the low poll score probably reflects the fact that most companies already have solutions in place for vendor access. The explosion of remote workers, however, is raising concern about privileges and security of external systems. Leveraging IT’s expertise and solutions for this offers a significant opportunity to improve security with minimal costs.
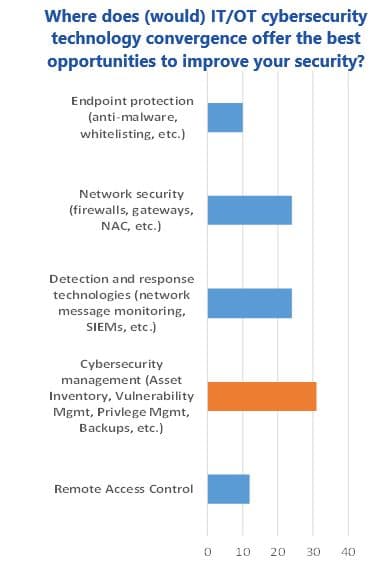 Management of the security of IoT and mobile devices could also be improved through use of more advanced network security products. Current OT equipment, however, cannot support features like network access control (NAC) and encryption, so introduction of this technology could require expensive upgrades of OT equipment. Better security is generally not enough to justify the costs and disruptions of OT system upgrades.
Management of the security of IoT and mobile devices could also be improved through use of more advanced network security products. Current OT equipment, however, cannot support features like network access control (NAC) and encryption, so introduction of this technology could require expensive upgrades of OT equipment. Better security is generally not enough to justify the costs and disruptions of OT system upgrades.
This Insight highlighted some of the findings of the ARC Industry Forum IT/OT cybersecurity technology convergence workshop. The session’s polls and roundtable discussion provided a wealth of additional information that can help industrial companies build cybersecurity convergence strategies. Roundtable panelists included practicing cybersecurity end users from a diverse set of major industrial companies, including Jeff Aiken of BASF, Eric Devoy of BP, Jarrett Lawrence of ExxonMobil, Jeff Nalazek of Dow Chemical, and Dan Rozinski, previously with Dow Chemical.
Every person involved in industrial cybersecurity should make it a point to watch a replay of this extremely informative workshop. We also recommend that you explore all the cybersecurity sessions at the recent ARC Industry Forum by registering for the ARC 2021 Industry Forum through our event site. Registration will also give you access to recordings of sessions on a variety of other topics in digital transformation, OT technology developments, smart cities, and supply chain.
For further information or to provide feedback on this Insight, please contact your account manager or the author at [email protected]. ARC Insights are published and copyrighted by ARC Advisory Group. The information is proprietary to ARC, and no part may be reproduced without prior permission from ARC.
ARC Advisory Group clients can view the complete report at ARC Client Portal.
If you would like to buy this report or obtain information about how to become a client, please Contact Us
Keywords: IT/OT Cybersecurity Convergence, ARC 2021 Industry Forum, ARC Advisory Group.

